In order to protect the assets of our organization in cyberspace, it is necessary to first understand the basic concepts.
We define cyberspace as a complex environment created by the interaction of people, software and services on the Internet, with the help of connected equipment and networks that do not exist in any physical form.
Cybersecurity is the preservation of the confidentiality, integrity and availability of information in cyberspace.
The following figure shows the relationship between cybersecurity and other security domains.
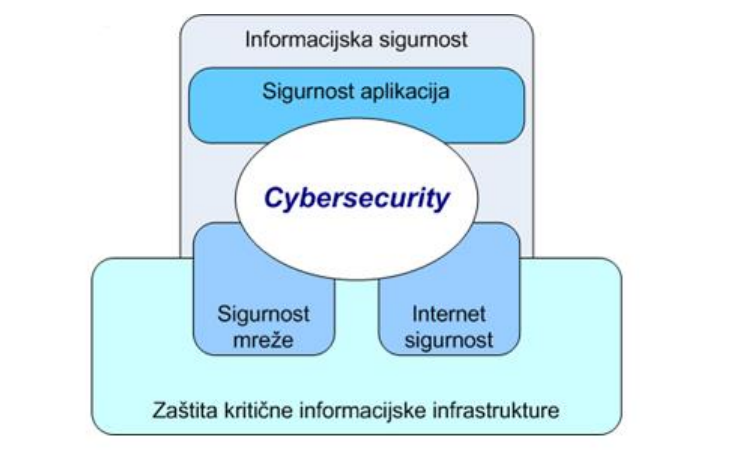
When we understand the basic concepts and relationship between cybersecurity and other security domains, we need to identify cyberspace threats, attack mechanisms, and key actors.
Threats in cyberspace can be directed at individuals or organizations, ie their property, which can be in physical or virtual form.
Best practices in the field of preventive, detective and reactive action can be used as measures to protect property.
Research has shown that 43% of cyber-attacks are targeted at small businesses and that the most expensive component of cyber-attacks is information loss, which accounts for 43% of costs.
ISO 27032 standard provides instructions for the preparation of cybersecurity programs, the implementation of which can achieve the desired level of security in cyberspace. The norm indicates a very complex relationship between cybersecurity and other security domains. Cybersecurity is also closely linked to Internet security, network security and information security in general. This standard starts from the identification of assets in cyberspace and the identification of potential cyber-threats and risks, and provides guidelines for selecting appropriate measures that reduce the likelihood of cyber-threats.
Threats to personal property in cyberspace may include theft or leakage of personal data, identity theft, sale of data on the black market, unauthorized access to a person’s financial data (theft of money, fraud), attack on an avatar or virtual currency for real value conversion, „Virtual theft“ and „Virtual mugging”, turning a personal computer into a zombie / bot, etc.
Threats to organizational assets in cyberspace can be compromising the integrity and availability of the organization’s website, stealing and reselling the organization’s URLs, stealing personal data of employees, clients, partners, etc., disclosing confidential data resulting in regulatory violations and financial consequences, data theft of national importance through e-government services, etc.
These threats seek to exploit system vulnerabilities through various attack mechanisms to destroy, detect, alienate, disable, gain unauthorized access or misuse property.
Attack mechanisms can come inside or outside the private network.
An example of an attack within a private network is the abuse of administrator rights or the use of software techniques and tools (malware, key loggers, etc.) to gain passwords or other identity information within a private network.
Attacks outside the private network target what is available externally, and these can be routers, servers, firewalls, Web, etc. Some examples are “port scanners” that scan all ports on the server and look for those that are open (one of their purposes Denial of Service attack using bots). It is also possible the so-called. “Buffer overflow” method of compromising the server by sending a much longer string than expected, which causes uncontrolled mode and allows the insertion of malicious code. “IP spoofing” is also used, ie manipulating IP addresses in an attempt to disguise a known source in order to gain unauthorized access to the system.
Also, with the increasing use of peer-to-peer file-sharing applications (photos, music, videos…), attacks are becoming more sophisticated and trying to disguise malicious code to other computers via “Trojan horses”.
In order to identify which cybersecurity measures to implement, a risk assessment needs to be conducted first. In order to conduct a risk assessment, it is necessary to identify critical assets because it is not cost-effective to protect all assets. When assessing risk, the organization should decide which methodology to use, and when choosing a methodology, the ISO 27005 standard can be used. It is important to understand that whatever risk management methodology the organization chooses, it will never prevent the occurrence of all risks, but will only identify the risks, their level and choose how to deal with risks. The risk management options are as follows:
- Implement appropriate risk mitigation measures
- Conscious and objective risk acceptance (if it meets the organization’s policy and risk acceptance criteria)
- Risk avoidance
- Transfer of risk to other parties, eg insurers or suppliers.
Risk assessment and management needs to be done on a regular basis, especially for an area such as cybersecurity, due to its dynamism and frequent changes.
If the organization decides on the risk reduction option when dealing with risks, then according to the ISO 27032 standard it can implement some of the following measures:
- Application-level controls
- A brief overview of basic online policies
- Secure handling of Web application sessions (cookies)
- Input Security Check (SQL Injection Prevention)
- Secure Web scripting (Cross-site Scripting prevention)
- Review and test code security
- Possibility of authentication of the service by the user (sub-domain, https…)
- Server security configuration (access control, logs…)
- Implement a system of testing and lifting security upgrades
- Monitor server security performance through regular log review
- Implementation of controls against malicious code on the server (anti-virus, anti-spyware)
- Implement vulnerability testing of online applications
- Controls for end users
- Use a supported operating system and applications, with regularly updated security patches
- Using anti-virus and anti-spyware tools
- Enable script blocking / script acceptance only from verified sources
- Using phishing filters
- Using a personal firewall and HIDS
- Use other available Web browser security features, enable automatic updates, and more.
- Controls for protection against social engineering attacks (effective protection as a combination)
- Security policies
- Method and process for:
- Classification of information
- Awareness and education
- Testing
- Organizations and people
- Technical controls
- Controls to improve cyber security readiness
- Darknet monitoring (a set of IP addresses that are not used in the organization)
- Black Hole Monitoring
- Low and High Interaction Monitoring
- Sinkhole Operation (redirection of specific IP traffic to the “sinkhole” device)
- Traceback (attack path reconstruction, attacker location, traffic correction…)
The organization can further improve its level of cybersecurity by using recommendations from other available methodologies and frameworks, such as ENISA, NIST Cybersecurity Framework, etc.
In order for the organization’s cyber-security program to give the desired results and constantly improve, it is necessary to regularly conduct risk assessments and monitor changes in the environment and the emergence of new threats and vulnerabilities that may occur due to changes in business, goals or assets.





