Homepage > Consulting > Information security, Cyber security and business continuity > Cyber security management
Cyber security management
What is cybersecurity?
Cyber security concerns the protection of systems, networks and SW against digital attacks aimed at accessing, altering or destroying sensitive information, extorting money from users or disrupting normal business processes.
One of the safeguards against cyber attacks is the application of cyber security controls. Cybersecurity is a system of organisational and technical activities and measures that achieve the authenticity, confidentiality, integrity and accessibility of data, as well as of network and information systems in the cyberspace or virtual space within which communication between network and information systems takes place and covers all network and information systems regardless of whether they are connected to the Internet.
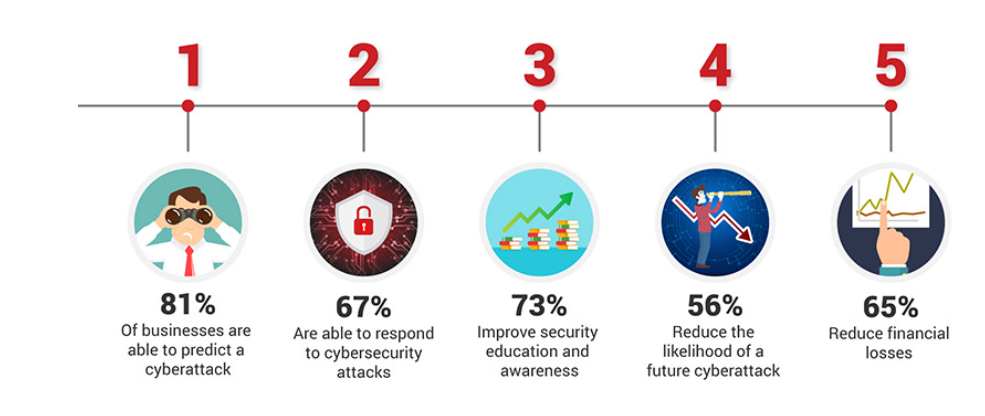
Izvor: www.pecb.com
Cyber threats
Cyber threats are continuing to increase globally, with different types of cyber attacks becoming increasingly sophisticated and complex and affecting our daily lives and operations. Various malicious programs, computer fraud, personal and financial data misuse, and social media misuse are just a few of them.
Cyber threats are divided into four categories:
Cybercrime – computer–aided crime. Most often, this category is associated with fraud involving internet banking and various fraud in web shops using other people‘s illegally acquired credit cards.
Cyber espionage – an action that provides covert information without the permission of the injured party. It is most commonly used in industry to gain an advantage over the competition by exploring the product that will be placed on the market and attempting to make the same or better product before the competition can place it. Cyber espionage is done using spyware, computer viruses, Trojan horses and various other means.
Cyber terrorism – planned and politically motivated attacks most often carried out by national groups.
Cyberwar – a war fought by computers and computer networks. It‘s an information war trying to gain an information advantage over an opponent of war. One way to do this is by stealing and altering opposing information.

ISO 27032 Standard
ISO 27032 Standard refers to cyber security, i.e. cyber security, defined as protection of privacy, integrity and availability of data in cyber space.
The standard provides guidance to improve the state of cybersecurity, highlighting the unique aspects of this activity and its dependence on other security domains:
information security,
network security,
internet security, and
protection of critical information infrastructure.
The standard shall ensure the following areas of cybersecurity:
cybersecurity screening; an explanation of the relationship between cybersecurity and other types of security;
the definition of stakeholders and a description of their role in cybersecurity;
guidelines to address common cybersecurity issues; and
a framework that will allow stakeholders to cooperate on cybersecurity issues.
How can ZIH help you?
ZIH can be a reliable partner in the development and implementation of ISO 27032 systems through the following consulting services:
Assessment of the current situation and preparation of GAP analysis against standards requirements
Preparation of project implementation of cyber security management system
Training of deployment team
Assessment of cyber risks
Development of system documentation
Participation in the implementation of the system
Preparations for certification of ISO 27032 systems (internal audits, remediation of non–conformities, management assessment)
Participation in certification
Participation in continuous system upgrades
Education in the following field:
- Compliance with the EU Regulation and the Cybersecurity Act
- How to apply the Cybersecurity Act and Regulation to operators of essential services and digital service providers
- Internal monitoring (audit) of cybersecurity of critical service operators and digital service providers
- What cybersecurity is and how to implement it into your own business
- How to set up a cybersecurity system
- Audit of cyber security systems
- Certified ISO 27032 Cybersecurity Foundation (PECB)
- Certified ISO 27032 Lead Cybersecurity Manager (PECB)
- Lead Ethical Hacker (PECB)
You may also be interested in these services and trainings:
Why ZIH?
ZIH has extensive experience in projects that include preparation of implementation of cyber security management system, i.e. implementation of state analysis and implementation of security measures in accordance with the standard and legal regulations.



Contact us
Fill out the form and our staff will contact you and arrange a visit or online meeting to find out how we can help you.
We want to share with you our experiences and the latest trends that can help you in your daily business.




