Homepage > Consulting > Information security, Cyber security and business continuity > Alignment with the EU regulation 2016/1148, the law and the regulation on cyber security
Alignment with the EU regulation 2016/1148, the law and the regulation on cyber security
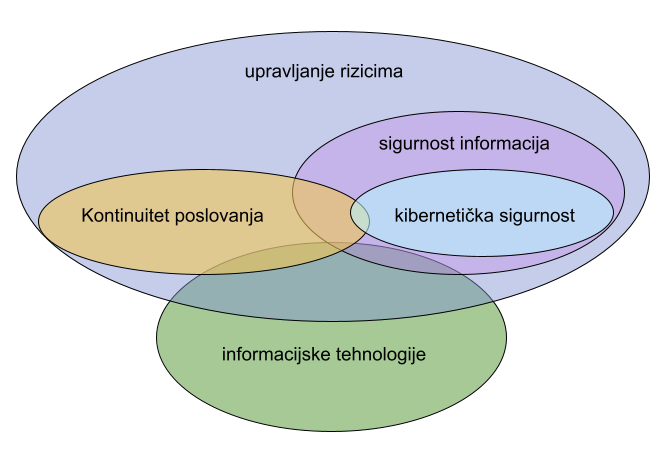
What is cybersecurity?
As more and more organisations are now focusing on digital business, the amount of data generated and exchanged between organisations is growing rapidly and organisations have become the target of cyber attacks.
One of the safeguards against cyber attacks is the application of cyber security controls. Cyber security is a system of organisational and technical activities and measures that achieve the authenticity, confidentiality, integrity and accessibility of data, as well as of network and information systems in the cyber space or virtual space within which communication between network and information systems takes place and covers all network and information systems regardless of whether they are connected to the Internet
In July 2018, pursuant to the Cybersecurity Act of operators of essential services and Digital Service providers, the Government of the Republic of Croatia adopted the Regulation on Cybersecurity of operators of essential services and Digital Service providers (OG No. 68/2018).
The Regulation regulates measures to achieve a high level of cyber security for operators of essential services, how they are implemented, criteria for identifying incidents that have a significant impact on the provision of essential services, the content of notifications and other relevant issues for the notification of incidents.

Who has to comply with the Regulation?
Pursuant to the Cybersecurity Act and Regulation, operators of essential services and digital service providers are obliged to act in the following sectors:
Energy (electricity, oil, gas)
Transport
Banking
Financial market infrastructures
Health care
Supply and distribution of drinking water
Digital infrastructure
Business services for governmental bodies
What are the responsibilities of operators of essential services pursuant to the Regulation?
In order to fully comply with the requirements of cybersecurity legislation, the following activities should be carried out:
Analysis of the existing situation (AS–IS), i.e. the current status of compliance
Development of security management policy for key systems
Definition of objectives and strategic guidelines for maintaining business continuity
Designation of the person responsible for establishing and managing the security of critical systems
Definition of powers and responsibilities in relation to the security of key systems
Defining the risk management process of key systems that includes:
Development of a methodology for risk assessment and processing
Identification of equipment, persons and activities related to key systems
Carrying out a risk assessment of identified equipment, persons and activities
Carrying out risk processing and identification of risk mitigation measures in accordance with the ISO 27001 standard
Defining the physical and environmental security management process of key systems
Defining the process of ensuring security of supply, namely the availability of equipment and other resources necessary for the operation and maintenance of critical resources
Defining the contract relationship management process related to key resources
Definition of outsourcing management processes
Defining the process of controlling access to spaces and key systems
Definition of measures necessary for physical and logical separation of key systems
Defining the necessary safeguards for the protection of data processed, stored and transmitted in a key system
Definition of programme code protection measures
Definition of protection measures against disruption of availability of key systems
Defining the process of development and maintenance of key systems
Definition of project management processes
Defining the key system assembly asset management process
Defining change management processes
Definition of the configuration management process
Defining the continuity management process of key systems
Defining incident management processes
Definition of the reserve management process
Defining the process of preventive vulnerability checks of key systems
Defining the internal audit process
Conducting of training courses to raise awareness of cyber security
How can ZIH help you?
ZIH offers the following services in the following area:
Consulting services:
- A snapshot of the current situation (AS–IS) and GAP analysis that determines the level of current compliance/non–compliance of your organization with the requirements of the Cybersecurity Act and Regulation, and on the basis thereof defines the proposal for necessary activities for full harmonisation
- Implementation of the project to establish cybersecurity in your organization
Education in the following field:
You may also be interested in these services and trainings:
Why ZIH?
ZIH has extensive experience in projects that include preparation of implementation off documentation and content management system, through identification and modelling of business processes and development of technical specification of the system.


Contact us
Fill out the form and our staff will contact you and arrange a visit or online meeting to find out how we can help you.
We want to share with you our experiences and the latest trends that can help you in your daily business.




