Homepage > Consulting > Information security, Cyber security and business continuity > Information security risk management
Information security risk management
What is information security risk management?
Information security risk management is a set of coordinated activities by which the company is directed and controlled in order to conduct an effective assessment and resolution of information security risks over time.
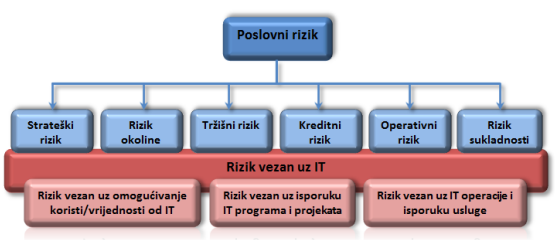
Information has become the most important currency of today and is the fundamental drive of every business system. Due to its imperative importance, it is necessary to establish a system of controls and measures in order to achieve an adequate level of protection irrespective of its form. Due to the inevitable application of information and communication technologies in almost all areas of life and in particular business, the security of information systems is particularly important, and should be considered as a basis for efficient and successful business operations. No system can be fully protected but measures can be taken to increase the level of protection. Regardless of the magnitude of the threat, it can always exploit a vulnerability of the system, causing some damage that can be negligible but also significant. Timely identification of vulnerabilities and threats enables the company to mitigate or prevent damage. The information security risk management process is not easy and is an important component for the successful functioning of the information system and thus the company itself. Information security protects information from a wide range of threats, in order to ensure business continuity, minimise business damage and maximise return on investment and create new business opportunities.
The main task of information security risk management is to meet security requirements that comply with the requirements of all stakeholders of the company, while determining an acceptable point of relation between investments in security controls and the cost in case of occurrence of a security incident or threat.
Standard ISO 27005 on information security risk management goes beyond specific passwords, firewalls, filters and encryption and describes a systematic approach to information security risk management and process design in accordance with its provisions is essential for the successful implementation of the information security management system. The set of ISO 27000 standards is strictly calibrated according to risk treatment, and it is important that companies assess risks at the outset and then before establishing risk management and treatment plans.
ISO 27005 has been developed to help companies implement a formal and documented risk assessment, treatment, acceptance, information and monitoring process.

What are the benefits of information security risk management?
ISO 27005 describes the processes constituting the information risk management system, which are:
the establishment of a context refers to the collection of relevant company information in order to define risk assessment criteria such as:
the strategic value and criticality of the information asset;
legal, regulatory and contractual obligations;
the importance of protecting information assets (accessibility, confidentiality and integrity);
the expectations of all stakeholders;
the impact of security events on business.
an information security risk assessment, through which:
determine the value of the information asset;
identify vulnerabilities and threats;
identify existing controls;
assess the potential consequences for a security event;
determines the priority of the risks and thus the order in which they are processed.
handling information security risks, whereby the company decides whether:
apply new or change existing controls;
accept the risk;
avoid risk by suspending activities leading to the occurrence of risk;
transfer and share the risk to third parties (e.g. insurance company).
the acceptance of residual risks after the implementation of the risk management;
informing all stakeholders about risks and how risks are handled;
the monitoring and reassessment of information security risks shall be carried out, inter alia, where:
added new information assets falling within the scope of risk management;
the value of the information asset has changed (increase, decrease or has become critical);
emerging knowledge of emerging vulnerabilities and threats;
an increased impact on business due to a potential security event;
there‘s been an information security breach.
By implementing the information security risk management system, the company:
recognises more effectively the threats and vulnerabilities of its information assets;
establish a framework to protect essential aspects of its business (operational, financial, reputational);
complies with regulatory and regulatory regulations (if any);
How can ZIH help you?
For each ZIH user, it has an individualised approach depending on its needs. In accordance with this, we organize workshops with management teams and, with the expert guidance of our consultants and the application of world reference recommendations, we help users successfully implement processes of systematic information security risk management.
Consulting services that we can provide you with:
preparing approaches to information security risk management;
establishing an information security risk management process;
the choice of a method for managing information security risks;
developing a procedure for information security risk management;
carrying out the identification of information security risks;
carrying out an information security risk assessment;
advice on the selection of controls and ways to mitigate information security risks;
developing a framework of responsibility for information security risks;
consultations in the implementation of solutions into practice;
an information security risk management audit;
Preparation of GAP analysis of compliance with regulatory, legal and other regulations and standards.
For the purpose of better mutual understanding, we organise workshops through which we provide users with guidelines on how to:
understand and define the context of their company‘s operations;
identify all key stakeholders;
identify the information asset, its value and importance;
identify the vulnerabilities, threats and risks of their business;
recognise operational risks of the use of ICT.
Education in the following field:
Why and how to manage information security risks?
Certified ISO 27005 Foundation (PECB)
Certified ISO 27005 risk Manager (PECB)
Certified ISO 27005 led risk Manager (PECB)
You may also be interested in these services and trainings:
Why ZIH?
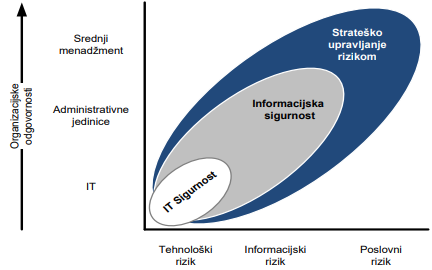
ZIH has more than 20 years of rich experience in shaping the modern organization of business risk management systems and in particular information security risks, and closely monitors the development and implementation of standards related to this topic (like ISO 31000, ISO 27005). It has also successfully carried out a number of assessments of business, information technology use and information security risks.











Contact us
Fill out the form and our staff will contact you and arrange a visit or online meeting to find out how we can help you.
We want to share with you our experiences and the latest trends that can help you in your daily business.